 Few posts ago, I have gone over the procedure needed to get OpenVPN going. However, what about SSTP-based VPN?
Few posts ago, I have gone over the procedure needed to get OpenVPN going. However, what about SSTP-based VPN?
This guide is going to assume you are to enter commands into the New Terminal window from WinBox. That way I will simply repeat commands needed instead of going through the screens. Commands are actually quite descriptive and easy to “translate” into GUI actions if that is your preference.
Prerequisite for any VPN server is to get certificates sorted. Procedure is exactly the same as for OpenVPN server setup with the slight difference being that common-name really matters. It must match either external IP or external host name - no exceptions.
For completeness sake, I will repeat the certificate creation steps here:
/certificate
add name=ca-template common-name=example.com days-valid=3650 key-size=2048 key-usage=crl-sign,key-cert-sign
add name=server-template common-name=*.example.com days-valid=3650 key-size=2048 key-usage=digital-signature,key-encipherment,tls-server
add name=client-template common-name=client.example.com days-valid=3650 key-size=2048 key-usage=tls-client
sign ca-template name=ca-certificate
sign server-template name=server-certificate ca=ca-certificate
sign client-template name=client-certificate ca=ca-certificateDepending on your router's speed, that sign command might time-out - nothing to worry about - just wait for CPU to drop below 100%. Or alternatively check the name of certificate - template part will disappear once signing is completed.
For later shenaningans, we will need root certificate export (just move it somewhere on your computer afterward):
/certificate
export-certificate ca-certificate export-passphrase=""Next we need a IP address pool for clients. I will assume you have your clients in some other network (e.g. 192.168.1.x) and this new network is just for VPN (notice that it can be the same pool as one used for OpenVPN):
/ip
pool add name="vpn-pool" ranges=192.168.8.10-192.168.8.99Instead of editing the default encrypted profile, we can create a new one. Assumption is your Mikrotik will also be a DNS server. And while at it, you can create a bit more imaginative user/password (again, if you did this for OpenVPN server, you can just reuse the same profile and user):
/ppp
profile add name="vpn-profile" use-encryption=yes local-address=192.168.8.250 dns-server=192.168.8.250 remote-address=vpn-pool
secret add name=user profile=vpn-profile password=passwordFinally, we get to enable SSTP VPN server interface - first step that is actually needed if you already have OpenVPN server running:
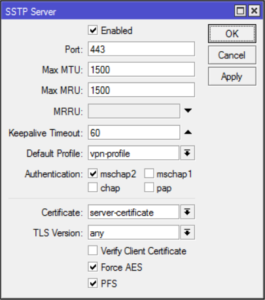
/interface sstp-server server
set enabled=yes default-profile=vpn-profile authentication=mschap2 certificate=server-certificate force-aes=yes pfs=yesOne curiosity is force-aes flag that is officially listed as not working with Windows clients. I've tested it on Windows 7 and 10 without any issues. You can clear it if you play with something older.
With this, our SSTP VPN server is up and running - onto the client setup!
For client we first need to import our certificate authority and we need to do it a bit roundabout way. First we start MMC (Microsoft Management Console) using mmc.exe and to it add Certificates (File->Add/Remove Snap-in). When asked select Computer account for Local Computer and find Trusted Root Certification Authorities. Right-click on it will show Import to which we give certificate we've exported a few steps ago.
In the Network and Sharing Center now we can go and Set up a new connection. When asked we just select Connect to a workplace and write destination host name (or IP). Remember that it must match certificate common-name (or a matching wildcard) you gave to your server certificate.
If all steps went fine, you should be presented with user name / password prompt and off you go.
PS: Do not forget to adjust firewall if necessary (TCP port 443).
/ip firewall filter
add chain=input protocol=tcp dst-port=443 action=accept place-before=0 comment="Allow SSTP"[2017-01-26: Adjusted certificate creation to work on RouterOS 6.38 and later]
[2017-01-26: Changed key size to 2048 (instead of 4096) so it doesn't take ages to generate certificates. :)]
Thank you for this. Saved us from some frustration as the mikrotik wiki was not explicit about what key-usages ought to be included when creating certificates. I’ve posted our experience here: http://forum.mikrotik.com/viewtopic.php?f=2&t=118405
Certificates no working on windows 10 error: CN name does no match transmited value
“example.com” was replaced by my dyndns name.
router RB750Gr3 firmware 6.38.3
Ernesto
Are you using your DynDNS name to connect? Your CA needs to have domain only (dyndns.org I guess in your case) while server certificate should be either exact DynDNS name or (my preference) wildcard.
Hi Josip,
After I’d installed the ca.crt on Trusted Root Certification Authorities and try to connect, I get the error:
“A certificate chain processed but terminated in a root certificate which is not trusted by the trust provider”.
I repeated 3 times your procedure but never works. Tried on a different RB but same problem. Version 6.37.4 of RouterOS. Have any idea what could be ?
Note: I did your OpenVPN tutorial and it is working fine in the same RB.
Thanks.
Did you install certificate under Local Machine or Local User? Try exporting server certificate and check how it looks on Windows. If it is ok you should see that certification path is green.
thanks boss
i can ping the MT and connecting it works. I cannot ping other IPs in the same net as the MT is. Do i need any firewall or routing?
Tried it, without success… ;-)
Proxy-ARP was the solution!
Bad solution of course. The right solution is to set up proper routing.
hi,
why did you create client certificate if you don’t use it?
tnx
Because this post was intended to be alternative to OpenVPN one and there you do need client certificate. I tried to keep those two posts very close so one can either use the same certificates for both or switch back-and-forth between them without needing to repeat certificate creation.
ok. thanks a lot.
I am having trouble resolving host names. I can ping IP addresses for devices on the MikroTik’s network, but not their hostnames. Any idea on what I may need to do?
i setup L2TP Server,
computer can connecting to Mikrotik ,
but cellphone can not connect.
Be careful with the L2TP over IPSEC.
Because it’s NAT sensitive…
I mean one connection is possible to Server from the same NAT…
You’re awsome.
Thank you very much for this tutorial.
My vpn connects fine, but I can’t ping or access any equipment behind the Mikrotik, I can’t even access the Mikrotik by Winbox.
I already change the interface to Proxy-ARP, like one of the users said, but it still doesn’t work. Can you please help me?
Ok I changed Bridge do Proxy-ARP and now I can ping the other equipments behind the Mikrotik, but I still can’t access the Mikrotik by web or by Winbox
I found the problem, the firewall was blocking me.
If anyone has the same problem, you just have to create a rule do allow access to the winbox port.
/ip firewall filter
add action=accept chain=input comment=”Allow Access to Winbox from VPN” dst-port=8291 protocol=tcp src-address=192.168.0.0/24 src-port=””
Hi,
Thank you for the good article. I’m using mikrotik 6.40.4 with Windows x64 SP1 as client. I want to ask the following:
1. Do I have to setup the IP addresses manually? (192.168.8.250 in your example)
2. I get also:
“A certificate chain processed but terminated in a root certificate which is not trusted by the trust provider”.
I generated with this:
/certificate
add name=ca-template common-name=tbrook days-valid=3650 key-size=2048 key-usage=crl-sign,key-cert-sign
add name=server-template common-name=*.tbrook days-valid=3650 key-size=2048 key-usage=digital-signature,key-encipherment,tls-server
add name=client-template common-name=client1.tbrook days-valid=3650 key-size=2048 key-usage=tls-client
sign ca-template name=ca-certificate
sign server-template name=server-certificate ca=ca-certificate
sign client-template name=client-certificate ca=ca-certificate
Imported only file cert_export_ca-certificate.crt in “Trusted Root Certification Authorities”
in Windows VPN I have specified the tbrook as hostname. Any idea?
Mikrotik hostname is also tbrook
I somehow imported it wrongly under local user. Now the cert is under local computer, but I get this:
“The Ceritifactes CN name does not match the passed value.
Obviously I’m generating the certificates in with wrong CN’s. I use tbrook everywhere and connect using tbrook instead of IP. Still the same error. Suggest something, please.
I believe this is due to a single name hosts – these are not necessarily resolved via Windows DNS. I wrote a bit about that in Adding Domain Search Option to Mikrotik DHCP and Local Host Name Resolving Under Windows With Mikrotik’s DNS.
Alternatively, if you don’t want through that trouble, try making all your certificates use more than a single word for domain name, e.g.:
/certificate
add name=ca-template common-name=sstp.tbrook days-valid=3650 key-size=2048 key-usage=crl-sign,key-cert-sign
add name=server-template common-name=*.sstp.tbrook days-valid=3650 key-size=2048 key-usage=digital-signature,key-encipherment,tls-server
add name=client-template common-name=client1.sstp.tbrook days-valid=3650 key-size=2048 key-usage=tls-client
I’m testing right away!
Thanks for the tip!
Managed to figure it out:
1. Maybe it is a good point to make sure the time on the Mikrotik is absolutely correct.
2. add name=server-template common-name=my_server_dns_or_ip days-valid=3650 key-size=2048 key-usage=digital-signature,key-encipherment,tls-server
my_server_dns_or_ip – here you need to match connection string as it is being it an IP or DNS name
The strange thing is that client certificate does not affect the successful connection in any way. Please explain the need for commands:
/certificate
add name=client-template common-name=client1.tbrook days-valid=3650 key-size=2048 key-usage=tls-client
sign client-template name=client-certificate ca=ca-certificate
Thanks,
Todor
The client I’m testing from is from another area and I’m using a public IP address. I believe certificate checking happens before VPN DHCP address assignment to the client.
That’s why I tried your second suggestion to create the certs with sstp.tbrook
/system identity set name=sstp.tbrook
/certificate
add name=ca-template common-name=sstp.tbrook days-valid=3650 key-size=2048 key-usage=crl-sign,key-cert-sign
add name=server-template common-name=*.sstp.tbrook days-valid=3650 key-size=2048 key-usage=digital-signature,key-encipherment,tls-server
add name=client-template common-name=client1.sstp.tbrook days-valid=3650 key-size=2048 key-usage=tls-client
sign ca-template name=ca-certificate
sign server-template name=server-certificate ca=ca-certificate
sign client-template name=client-certificate ca=ca-certificate
/ip
pool add name=”vpn-pool” ranges=10.30.0.2-10.30.0.10
/ppp
profile add name=”vpn-profile” use-encryption=yes local-address=10.30.0.250 dns-server=10.30.0.250 remote-address=vpn-pool
secret add name=client1 profile=vpn-profile password=TestPass
/interface sstp-server server
set enabled=yes default-profile=vpn-profile authentication=mschap2 certificate=server-certificate force-aes=yes pfs=yes
/certificate
export-certificate ca-certificate export-passphrase=””
After that I copy only certificate cert_export_ca-certificate.crt on the Win7 machine and import it under:
Certificates (Local Computer) -> Trusted Root Certification Authorities
I also modify my c:\windows\system32\drivers\etc\hosts and add entry a static entry for sstp.tbrook
In Windows SSTP VPN client I am using sstp.tbrook as hostname for destination
Error is again 0x800B010F The certificate’s CN name does not match the passed value.
I tried to enable logging in Mikrotik but see only this in the logs:
sstp,ppp,debug: LCP lowerdown
sstp,ppp,debug: LCP down event in initial state
Never saw this error before. However, I did see similar problem appear due to DHCP client on PPPoE port.
I have exactly the same problem as you, did you manage to figure out the solution?
i have the same problem
I cannot access it from other WAN
Great job – helped me a lot.
Only problem was. If I have server-certificate in the SSTP server I can’t connect, but if I select ca-certificate it works fine.
in the windows client I have imported the CA certificate as per the instructions in the guide.
Anyone, who can give me a hint why this is so.
This is a great article that I still use for setting this up on new routers. Just a note, on version 7 of RouterOS, they have remove AES altogether.