 Having OpenVPN server on your router is a nifty feature. However, as often with Mirotik, not all is straight forward.
Having OpenVPN server on your router is a nifty feature. However, as often with Mirotik, not all is straight forward.
This guide is going to assume you are to enter commands into the New Terminal window from WinBox. That way I will simply repeat commands needed instead of going through the screens. Commands are actually quite descriptive and easy to “translate” into GUI actions if that is your preference.
Prerequisite for any VPN server is to get certificates sorted. For OpenVPN we need main Certificate Authority, server, and client certificate. Yes, strictly speaking, client certificate is optional but let's not skimp on security.
First we create all the certificate templates (10 years validity) we'll need:
/certificate
add name=ca-template common-name=example.com days-valid=3650 key-size=2048 key-usage=crl-sign,key-cert-sign
add name=server-template common-name=*.example.com days-valid=3650 key-size=2048 key-usage=digital-signature,key-encipherment,tls-server
add name=client-template common-name=client.example.com days-valid=3650 key-size=2048 key-usage=tls-clientFor the purpose of OpenVPN server common name can be really anything. However, some other VPNs are not as forgiving (yes SSTP, I am looking at you) so it might be best to have either your external IP or host name as the common-name text. Any yes, if you have dynamic IP and you are not using your own domain, you can put *.dyndns.org there - no worries.
Created certificates will need signing:
/certificate
sign ca-template name=ca-certificate
sign server-template name=server-certificate ca=ca-certificate
sign client-template name=client-certificate ca=ca-certificateDepending on your router's speed, that sign command might time-out - nothing to worry about - just wait for CPU to drop below 100%. Or alternatively check name of certificate - template part will disappear once signing is completed.
With this we need to export a few files:
/certificate
export-certificate ca-certificate export-passphrase=""
export-certificate client-certificate export-passphrase=12345678This should give you three files: cert_export_ca-certificate.crt, cert_export_client-certificate.crt, and cert_export_client-certificate.key. After copying this on computer for later I like to rename them to ca.crt, client.crt, and client.key respectively.
Next we need a separate pool of IP addresses for clients. I will assume you have your clients in some other network (e.g. 192.168.1.x) and this new network is just for VPN:
/ip
pool add name="vpn-pool" ranges=192.168.8.10-192.168.8.99Instead of editing the default encrypted profile, we can create a new one. Assumption is your Mikrotik will also be a DNS server. And while at it, you can create a bit more imaginative user/password:
/ppp
profile add name="vpn-profile" use-encryption=yes local-address=192.168.8.250 dns-server=192.168.8.250 remote-address=vpn-pool
secret add name=user profile=vpn-profile password=passwordFinally, we can enable OpenVPN server interface:
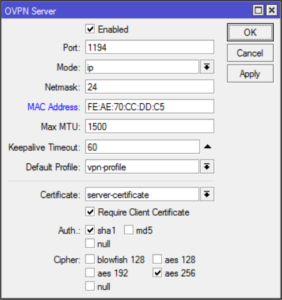
/interface ovpn-server server
set default-profile=vpn-profile certificate=server-certificate require-client-certificate=yes auth=sha1 cipher=aes128,aes192,aes256 enabled=yesNow finally we can copy both ca.crt and client.crt to C:\Program Files\OpenVPN\config\ directory alongside client.ovpn.
You don't have client.ovpn? Well, one is in sample-config directory and we just need to change/add highlighted items:
client
dev tun
proto tcp
remote example.com 1194
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert client.crt
key client.key
remote-cert-tls server
cipher AES-128-CBC
auth SHA1
auth-user-pass
redirect-gateway def1
verb 3A bit annoying step is being asked for the private key passphrase (in the addition to username/password). Mikrotik doesn't allow export without it but fortunately we can use OpenSSL to change that:
> openssl.exe rsa -in client.key -out client.key
Enter pass phrase for client.key: 12345678
writing RSA keyWith this, your VPN connection should work like a charm.
PS: Do not forget to adjust firewall if necessary (TCP port 1194).
/ip firewall filter
add chain=input protocol=tcp dst-port=1194 action=accept place-before=0 comment="Allow OpenVPN"PPS: Do check SSTP guide too.
PPPS: If you're on RouterOS 7 you might want to check this guide for UDP.
[2017-01-26: Adjusted certificate creation to work on RouterOS 6.38 and later]
[2017-01-26: Changed key size to 2048 (instead of 4096) so it doesn't take ages to generate certificates. :)]
[2017-02-25: Changed example to use AES-128 for lower CPU usage on router.]
Because i had problems with TSL i added the following line to the .ovpn file
tls-cipher DEFAULT
Thanks! Worked perfectly.
I just suggest to replace the port 1194 to 443 to bypass some firewall blocks.
you are the best. may god be with you.
“A bit annoying step is being asked for the private key passphrase (in the addition to username/password). Mikrotik doesn’t allow export without it but fortunately we can use OpenSSL to change that:
> openssl.exe rsa -in client.key -out client.key
Enter pass phrase for client.key: 12345678
writing RSA key”
Where do you do this step? On any linux system?
You can do it on any Linux system or install openssl on Windows (e.g. as part of Git).
And for mac? i did that step like this
export-certificate client-certificate export-passphrase=””
But it didn’t export enything and its not conecting to opvn server, any help here?
You need to have a password specified when exporting. Otherwise a private key will not be exported.
thanks. Yes it doesn’t export, but how can i do ir if i dont have windows?
hi, still clueless how to edit this using OpenSSL, already download and instaled in my windows but i dont know how to use it. please help
i set my ip range from 10.10.10.1-30 and 10.10.10.25 as gateaway and dns
thank you
use this site to generate your config e decrypt the certificate: https://ovpnconfig.com.br.
Hi Josip,
Is it possible to revoke the user certificate and block their vpn access on mikrotik side, instead of resetting the PPP Secret password? I tryed to revoke the user certificate on mikrotik but the user continue accessing the VPN!
Thank you!
Not really – client certificate is not checked upon access.
Maybe disable that user account or change password?
Great OpenVPN tutorial. Thx
I had run in to a problem regarding clients subnet. On widows client in log:
There is a problem in your selection of –ifconfig endpoints [local=192.168.8.99, remote=192.168.8.250]. The local and remote VPN endpoints must exist within the same 255.255.255.252 subnet. This is a limitation of –dev tun when used with the TAP-WIN32 driver. Try ‘openvpn –show-valid-subnets’ option for more info.
Problem was solved by moving pool to
pool add name=”vpn-pool” ranges=192.168.8.240-192.168.8.249
Thanks for the tutorial.
Could I ask whether local-address=192.168.8.250 is the address of the Mikrotik box?
My Mikrotik box is behind a router. The Router is 192.668.1.1, the Mokrotik box is 192.668.1.15. What local-address do I use?
Charles
mistake…. should have been: The Router is 192.168.1.1, the Mikrotik box is 192.168.1.15
Can someone help me please?
I got this err message
*input does not match any value of certificate*
when running
*/interface ovpn-server server
set default-profile=vpn-profile certificate=server-certificate require-client-certificate=yes auth=sha1 cipher=aes128,aes192,aes256 enabled=yes*
What could be wrong ??
It looks as if command cannot find certificate under name “server-certificate”. Did you name it something else?
Awesome, thank you ;)
Hi Josip,
I’m having issue with port 443, i can connect using other port (465 or 587) but for reason, 443 just kept getting rejected.
Any ideas ?
This is the error msg
2017-11-09 13:49:19: TCP/UDP: Preserving recently used remote address: [AF_INET]61.0.0.000:443
2017-11-09 13:49:19: Attempting to establish TCP connection with [AF_INET]61.0.0.000:443 [nonblock]
2017-11-09 13:49:20: State changed to Disconnecting
2017-11-09 13:49:20: SIGTERM[hard,init_instance] received, process exiting
2017-11-09 13:49:20: State changed to Disconnected
Probably something else is running on it. Try “netstat -nap | grep LISTEN” to see what is there.
Hi, how about:
client:
Connection reset, restarting [0]
Sun Nov 12 22:31:19 2017 us=380382 TCP/UDP: Closing socket
Sun Nov 12 22:31:19 2017 us=380498 SIGUSR1[soft,connection-reset] received, process restarting
server:
: terminating… – could not add address list: empty list name not allowed (6)
Based on server message alone, it looks as IP address pool might not be set.
Thanks for the guide, I’m relatively inexperienced and have been trying to get OpenVPN to work and this is the closest I’ve come so far.
I’ve set it all up and I can connect, but my Internet on the remote computer is being routed through the Mikrotik and I cannot access/ping the Mikrotik or any computers on the Mikrotik’s network. I want it to be the other way around.
The Mikrotik manages the network 192.168.10.0/24 and the OpenVPN server is set up to give out address on 192.168.8.0/24. When I dial in via VPN, I only want traffic to 192.168.10.0/24 to be routed over the VPN, the rest (i.e. Internet) must NOT go through the VPN. How do I change your configuration to achieve this?
I don’t believe you can do it with Mikrotik’s configuration.
What you want is split tunneling and that must be configured on connecting machine (afaik). There are a few guides about it on internet, e.g. this one.
In short, you must set your computer to route only subset of addresses via VPN while all other are going over normal connection; e.g.192.168.0.0/16 via VPN; 0.0.0.0 via Normal.
It’s easy to setup. Just add one route on MikroTik with destination address range you want, and VPN interface as gateway.
This is a great set up and seems to work just fine. However it seems to require a new profile for every device you want to connect. For instance if I wanted to connect both my phone and my laptop I would need two separate profiles (due to local address being static). Is there a way to set this up with the local address being a pool as well?
Local address can be static for multiple devices at the same time. All that matters is remote address and for that one we do use a pool.
Hi,
seems that
> sign ca-template name=ca-certificate
needs some external certificate? Would be great to have this hinted in your doc :)
-h
It doesn’t need external certificate. This step creates root certificate needed from the ca-template defined in box above.
Excellent tutorial – thank you very much :-)
How can I set this up so that the VPN users can access computers on the LAN once the VPN has been established?
-Aang
Enable proxy-arp on the bridge interface.
hi
thanks for your great tutorial
I can’t connect to the server, the log file shows the error ” duplicate packet, dropping”!!
what is the problem?????
thank you
This usually indicates issue on client. Do check OpenVPN client log for clues.
here is log file for last try
<<<8192] S=[8192->8192]
Tue Jan 02 21:48:15 2018 us=902108 Attempting to establish TCP connection with [AF_INET]82.102.14.x:1194 [nonblock]
Tue Jan 02 21:48:15 2018 us=902108 MANAGEMENT: >STATE:1514917095,TCP_CONNECT,,,,,,
Tue Jan 02 21:48:16 2018 us=903165 TCP connection established with [AF_INET]82.102.14.x:1194
Tue Jan 02 21:48:16 2018 us=903165 TCP_CLIENT link local: (not bound)
Tue Jan 02 21:48:16 2018 us=903165 TCP_CLIENT link remote: [AF_INET]82.102.14.x:1194
Tue Jan 02 21:48:16 2018 us=903165 MANAGEMENT: >STATE:1514917096,WAIT,,,,,,
Tue Jan 02 21:48:16 2018 us=904165 MANAGEMENT: >STATE:1514917096,AUTH,,,,,,
Tue Jan 02 21:48:16 2018 us=904165 TLS: Initial packet from [AF_INET]82.102.14.x:1194, sid=7846b6ff d01f4dd3
>>>>>>>
after last line the error message appears on server log
thanks
try increasing debug level – e.g. by setting verb to 6 or higher.
thank you so much
I set verb to 10 and this is log:
<<len=0 wakeup=604800
Fri Jan 05 11:35:10 2018 us=136129 ACK reliable_can_send active=1 current=0 : [2] 1
Fri Jan 05 11:35:10 2018 us=136129 ACK reliable_send_timeout 8 [2] 1
Fri Jan 05 11:35:10 2018 us=136129 TLS: tls_process: timeout set to 8
Fri Jan 05 11:35:10 2018 us=136129 TLS: tls_multi_process: i=1 state=S_INITIAL, mysid=bf536d1c 5748c9b3, stored-sid=00000000 00000000, stored-ip=[AF_UNSPEC]
Fri Jan 05 11:35:10 2018 us=136129 NOTE: –mute triggered…
>>>
much appreciated :)
the entire log does not show up here
in the following link there is the log file in my Drive
https://docs.google.com/document/d/1hZI72uBtfnhfWVEsPMQAjlCLxQ3_QCCO9IGq3_3mmW8/edit?usp=sharing
Based on your log, it seems server doesn’t like encryption options. It seems you are using cipher AES-256-CBC and server doesn’t like it. Please check if your mikrotik has aes256 enabled, either via UI or via command line:
> /interface ovpn-server server> print
enabled: yes
port: 1194
mode: ip
netmask: 24
mac-address: XX:XX:XX:XX:XX:XX
max-mtu: 1500
keepalive-timeout: 60
default-profile: vpn-profile
certificate: vpn-server-certificate
require-client-certificate: yes
auth: sha1
cipher: aes128,aes256
thank you very much
it has been connected successfully
but my traffic does not go through ovpn
based on this config what’s the problem?
client
dev tun
proto tcp-client
remote 82.102.14.x
port 1194
nobind
persist-key
persist-tun
tls-client
remote-cert-tls server
ca cert_export_CA.crt
cert cert_export_CLIENT1.crt
key cert_export_CLIENT1.key
mute 10
cipher AES-256-CBC
auth SHA1
auth-user-pass secret
auth-nocache
redirect-gateway def1
It is probably related to routing. I would advise you to check your routing tables (on both client and router) and to snoop traffic on each.
What usually works well for me is actually getting the simplest setup working before going to a more complicated one.
I get the following error if i try to connect from Windows 7 to my Mikrotik:
Sun Jan 28 20:23:28 2018 VERIFY OK: depth=1, CN=example.com
Sun Jan 28 20:23:28 2018 VERIFY KU OK
Sun Jan 28 20:23:28 2018 Validating certificate extended key usage
Sun Jan 28 20:23:28 2018 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Sun Jan 28 20:23:28 2018 VERIFY EKU OK
Sun Jan 28 20:23:28 2018 VERIFY OK: depth=0, CN=server
Sun Jan 28 20:23:28 2018 Connection reset, restarting [0]
Sun Jan 28 20:23:28 2018 SIGUSR1[soft,connection-reset] received, process restarting
Sun Jan 28 20:23:28 2018 MANAGEMENT: >STATE:1517167408,RECONNECTING,connection-reset,,,,,
Sun Jan 28 20:23:28 2018 Restart pause, 5 second(s)
Sun Jan 28 20:23:33 2018 TCP/UDP: Preserving recently used remote address: [AF_INET]84.112.18.105:1194
Sun Jan 28 20:23:33 2018 Socket Buffers: R=[8192->8192] S=[8192->8192]
Sun Jan 28 20:23:33 2018 Attempting to establish TCP connection with [AF_INET]IP-Address:1194 [nonblock]
Sun Jan 28 20:23:33 2018 MANAGEMENT: >STATE:1517167413,TCP_CONNECT,,,,,,
Sun Jan 28 20:23:34 2018 TCP connection established with [AF_INET]IP-Address:1194
Sun Jan 28 20:23:34 2018 TCP_CLIENT link local: (not bound)
Sun Jan 28 20:23:34 2018 TCP_CLIENT link remote: [AF_INET]IP-Address:1194
Sun Jan 28 20:23:34 2018 MANAGEMENT: >STATE:1517167414,WAIT,,,,,,
Sun Jan 28 20:23:34 2018 MANAGEMENT: >STATE:1517167414,AUTH,,,,,,
Sun Jan 28 20:23:34 2018 TLS: Initial packet from [AF_INET]IP-Address:1194, sid=a66ddb54 61ca445f
Sun Jan 28 20:23:36 2018 VERIFY OK: depth=1, CN=example.com
Sun Jan 28 20:23:36 2018 VERIFY KU OK
Sun Jan 28 20:23:36 2018 Validating certificate extended key usage
Does anyone have an idea whtat is wrong ?
Chris
I have the same problem
hello
my vpn connected but no internet acces . im using vps mikrotik can you help me?
To the point, thank you!
Excellent post. I have follow a lot of tutorials but it all give me the exact same “error”. Can someone help?
Mon Feb 19 18:06:30 2018 OpenVPN 2.3.18 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [PKCS11] [IPv6] built on Oct 26 2017
Mon Feb 19 18:06:30 2018 Windows version 6.2 (Windows 8 or greater) 64bit
Mon Feb 19 18:06:30 2018 library versions: OpenSSL 1.0.2l 25 May 2017, LZO 2.10
Enter Management Password:
Mon Feb 19 18:06:30 2018 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Mon Feb 19 18:06:30 2018 Need hold release from management interface, waiting…
Mon Feb 19 18:06:30 2018 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Mon Feb 19 18:06:30 2018 MANAGEMENT: CMD ‘state on’
Mon Feb 19 18:06:30 2018 MANAGEMENT: CMD ‘log all on’
Mon Feb 19 18:06:30 2018 MANAGEMENT: CMD ‘hold off’
Mon Feb 19 18:06:30 2018 MANAGEMENT: CMD ‘hold release’
Mon Feb 19 18:06:36 2018 MANAGEMENT: CMD ‘username “Auth” “s.messias”‘
Mon Feb 19 18:06:36 2018 MANAGEMENT: CMD ‘password […]’
Mon Feb 19 18:06:38 2018 MANAGEMENT: CMD ‘password […]’
Mon Feb 19 18:06:38 2018 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Mon Feb 19 18:06:38 2018 Socket Buffers: R=[65536->65536] S=[65536->65536]
Mon Feb 19 18:06:38 2018 MANAGEMENT: >STATE:1519063598,RESOLVE,,,
Mon Feb 19 18:06:40 2018 Attempting to establish TCP connection with [AF_INET]109.51.161.49:1194 [nonblock]
Mon Feb 19 18:06:40 2018 MANAGEMENT: >STATE:1519063600,TCP_CONNECT,,,
Mon Feb 19 18:06:50 2018 TCP: connect to [AF_INET]109.51.161.49:1194 failed, will try again in 5 seconds: Connection timed out (WSAETIMEDOUT)
Mon Feb 19 18:06:55 2018 MANAGEMENT: >STATE:1519063615,RESOLVE,,,
Mon Feb 19 18:06:55 2018 MANAGEMENT: >STATE:1519063615,TCP_CONNECT,,,
Mon Feb 19 18:07:05 2018 TCP: connect to [AF_INET]109.51.161.49:1194 failed, will try again in 5 seconds: Connection timed out (WSAETIMEDOUT)
Mon Feb 19 18:07:10 2018 MANAGEMENT: >STATE:1519063630,RESOLVE,,,
Mon Feb 19 18:07:10 2018 MANAGEMENT: >STATE:1519063630,TCP_CONNECT,,,
Mon Feb 19 18:07:20 2018 TCP: connect to [AF_INET]109.51.161.49:1194 failed, will try again in 5 seconds: Connection timed out (WSAETIMEDOUT)
Mon Feb 19 18:07:25 2018 MANAGEMENT: >STATE:1519063645,RESOLVE,,,
Mon Feb 19 18:07:25 2018 MANAGEMENT: >STATE:1519063645,TCP_CONNECT,,,
Mon Feb 19 18:07:35 2018 TCP: connect to [AF_INET]109.51.161.49:1194 failed, will try again in 5 seconds: Connection timed out (WSAETIMEDOUT)
As a first suggestion install latest OpenVPN client (2.4.4). Don’t use old clients. Can you post config details for server and client? Use e-mail If you wish privacy.
Br
Sasa
really simple & helpful, Thx a lot.
I don’t connect to ipfire firewall as client, can you help me? Thanks a lot
Man, you rock!
Works like a charm!
Many many thanks!!!
In command sign client-template name=client-certificate ca=ca-certificate i have got the message failure: name must be unique!. Whats my wrong?
Messages from openvpn. Cant connect. Whats the problem? Thanks
Fri Mar 16 17:58:45 2018 TCP_CLIENT link local: (not bound)
Fri Mar 16 17:58:45 2018 TCP_CLIENT link remote: [AF_INET]192.168.2.121:1194
Fri Mar 16 17:58:45 2018 MANAGEMENT: >STATE:1521215925,WAIT,,,,,,
Fri Mar 16 17:58:45 2018 MANAGEMENT: >STATE:1521215925,AUTH,,,,,,
Fri Mar 16 17:58:45 2018 TLS: Initial packet from [AF_INET]192.168.2.121:1194, sid=be91e965 fa86d7f8
Fri Mar 16 17:58:47 2018 VERIFY OK: depth=1, CN=example.com
Fri Mar 16 17:58:47 2018 VERIFY KU OK
Fri Mar 16 17:58:47 2018 Validating certificate extended key usage
Fri Mar 16 17:58:47 2018 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Fri Mar 16 17:58:47 2018 VERIFY EKU OK
Fri Mar 16 17:58:47 2018 VERIFY OK: depth=0, CN=casiosp.dvrdns.org
Fri Mar 16 17:58:47 2018 Connection reset, restarting [0]
Fri Mar 16 17:58:47 2018 SIGUSR1[soft,connection-reset] received, process restarting
Fri Mar 16 17:58:47 2018 MANAGEMENT: >STATE:1521215927,RECONNECTING,connection-reset,,,,,
Fri Mar 16 17:58:47 2018 Restart pause, 10 second(s)
Fri Mar 16 17:58:57 2018 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.2.121:1194
Fri Mar 16 17:58:57 2018 Socket Buffers: R=[65536->65536] S=[65536->65536]
Fri Mar 16 17:58:57 2018 Attempting to establish TCP connection with [AF_INET]192.168.2.121:1194 [nonblock]
Fri Mar 16 17:58:57 2018 MANAGEMENT: >STATE:1521215937,TCP_CONNECT,,,,,,
Fri Mar 16 17:58:58 2018 TCP connection established with [AF_INET]192.168.2.121:1194
Fri Mar 16 17:58:58 2018 TCP_CLIENT link local: (not bound)
Fri Mar 16 17:58:58 2018 TCP_CLIENT link remote: [AF_INET]192.168.2.121:1194
Fri Mar 16 17:58:58 2018 MANAGEMENT: >STATE:1521215938,WAIT,,,,,,
Fri Mar 16 17:58:58 2018 MANAGEMENT: >STATE:1521215938,AUTH,,,,,,
Fri Mar 16 17:58:58 2018 TLS: Initial packet from [AF_INET]192.168.2.121:1194, sid=68f041e5 8c91330d
Fri Mar 16 17:59:00 2018 VERIFY OK: depth=1, CN=example.com
Fri Mar 16 17:59:00 2018 VERIFY KU OK
Fri Mar 16 17:59:00 2018 Validating certificate extended key usage
Fri Mar 16 17:59:00 2018 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Fri Mar 16 17:59:00 2018 VERIFY EKU OK
Fri Mar 16 17:59:00 2018 VERIFY OK: depth=0, CN=casiosp.dvrdns.org
Fri Mar 16 17:59:01 2018 Connection reset, restarting [0]
Fri Mar 16 17:59:01 2018 SIGUSR1[soft,connection-reset] received, process restarting
Fri Mar 16 17:59:01 2018 MANAGEMENT: >STATE:1521215941,RECONNECTING,connection-reset,,,,,
Fri Mar 16 17:59:01 2018 Restart pause, 20 second(s)
Fri Mar 16 17:59:21 2018 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.2.121:1194
Fri Mar 16 17:59:21 2018 Socket Buffers: R=[65536->65536] S=[65536->65536]
Fri Mar 16 17:59:21 2018 Attempting to establish TCP connection with [AF_INET]192.168.2.121:1194 [nonblock]
Fri Mar 16 17:59:21 2018 MANAGEMENT: >STATE:1521215961,TCP_CONNECT,,,,,,
Fri Mar 16 17:59:22 2018 TCP connection established with [AF_INET]192.168.2.121:1194
Fri Mar 16 17:59:22 2018 TCP_CLIENT link local: (not bound)
Fri Mar 16 17:59:22 2018 TCP_CLIENT link remote: [AF_INET]192.168.2.121:1194
Fri Mar 16 17:59:22 2018 MANAGEMENT: >STATE:1521215962,WAIT,,,,,,
Fri Mar 16 17:59:22 2018 MANAGEMENT: >STATE:1521215962,AUTH,,,,,,
Fri Mar 16 17:59:22 2018 TLS: Initial packet from [AF_INET]192.168.2.121:1194, sid=13c51eb4 ef70e5e6
Fri Mar 16 17:59:23 2018 VERIFY OK: depth=1, CN=example.com
Fri Mar 16 17:59:23 2018 VERIFY KU OK
Fri Mar 16 17:59:23 2018 Validating certificate extended key usage
Fri Mar 16 17:59:23 2018 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Fri Mar 16 17:59:23 2018 VERIFY EKU OK
Fri Mar 16 17:59:23 2018 VERIFY OK: depth=0, CN=casiosp.dvrdns.org
Fri Mar 16 17:59:24 2018 Connection reset, restarting [0]
Fri Mar 16 17:59:24 2018 SIGUSR1[soft,connection-reset] received, process restarting
Fri Mar 16 17:59:24 2018 MANAGEMENT: >STATE:1521215964,RECONNECTING,connection-reset,,,,,
Fri Mar 16 17:59:24 2018 Restart pause, 40 second(s)
Hello.. the same problem… Did you solve it?
Best Regards
Hi,
try to add exact encryption cipher to client config.
in this case it is AES-128-CBC.
For me it solved the problem on both android and linux client.
Attempting to execute “sign client-template name=client-certificate ca=ca-certificate” I get:
“failure: certificate with the same subject exists!”
Thus, this cannot be signed.
Any suggestions?
Just use different name – you already has certificate named the same as one you are attempting to create from template.
Thanks. We used a workaround and have it working.
For the future – which field is the subject or name?
Appreciate the instructions on this.
What is your workaround? I keep running into this same error, and I do NOT have another certificate with the same name. It doesn’t matter what I name it; it doesn’t matter if I create a new one with a new name from scratch. It just keeps throwing the same error: “Couldn’t start – certificate with the same subject exists! (7)”
You need to set another “common name” for the client
same issue but im not sure, what to change really.
Hey Josip,
After running the export commands I only see two files: cert_export_ca-certificate.crt and cert_export_client-certificate.crt. There is no cert_export_client-certificate.key. Any ideas what’s wrong?
Did you use password? Certificates requires you to use a password in order to export private key.
Thanks for your submission!
We got an error:
Thu Apr 05 09:28:51 2018 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Thu Apr 05 09:28:51 2018 TCP/UDP: Preserving recently used remote address: [AF_INET]195.167.110.45:1194
Thu Apr 05 09:28:51 2018 Attempting to establish TCP connection with [AF_INET]########## [nonblock]
Thu Apr 05 09:28:52 2018 TCP connection established with [AF_INET]##################
Thu Apr 05 09:28:52 2018 TCP_CLIENT link local: (not bound)
Thu Apr 05 09:28:52 2018 TCP_CLIENT link remote: [AF_INET]##################
Thu Apr 05 09:28:54 2018 VERIFY ERROR: depth=0, error=unsupported certificate purpose: C=##, O=####, CN=##
Thu Apr 05 09:28:54 2018 OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
Thu Apr 05 09:28:54 2018 TLS_ERROR: BIO read tls_read_plaintext error
Thu Apr 05 09:28:54 2018 TLS Error: TLS object -> incoming plaintext read error
Thu Apr 05 09:28:54 2018 TLS Error: TLS handshake failed
Thu Apr 05 09:28:54 2018 Fatal TLS error (check_tls_errors_co), restarting
Thu Apr 05 09:28:54 2018 SIGUSR1[soft,tls-error] received, process restarting
Well, the solution is included in the log:
https://openvpn.net/index.php/open-source/documentation/howto.html#mitm
Hey thanks for the great post, this is an excellent walkthrough.
I am getting an error when I try to connect:
“Key file (‘client.key’) can be a maximum of 2048 bytes”
I have searched for a good hour now and not come up with any solution, do you know what would be causing this?
Try using key-size=2048 for key generation.
Hi! Thank you so much for this post! I’m connecting to my vpn and can see that my address is the static one (where my servers and Mikrotik are).
The only problem is that I’m not being able to do ssh or use RDP to the other machines that are on my remote end (my servers).
Seems to be something about routing, but I don’t know that much :/
Any tips?
I’m having this same issue.. I cannot access any server I have on the network I’m VPN’ing into. Internet access work but no access to local network machines.
Does anyone have any insight into how to access local machines on the local network we are VPN’ing into using this tutorial?
Much thanks in advance!
Same problem as Jhon…..
There is need to set NAT masquarade for srcnat chain with OpenVPN as a source network
Can you give an example and explain why should I set it?
Works a treat. Searched everywhere for decent instructions – this hits the spot. Well done, and thanks!
This should give you three files: cert_export_ca-certificate.crt, cert_export_client-certificate.crt, and cert_export_client-certificate.key. After copying this on computer for later I like to rename them to ca.crt, client.crt, and client.key respectively.
This did not give me a client.key
Did you set export password to something non-blank? For client.key to be exported, you need the export password.
I got it firgured out I tried to put a password on the ca too
Hello
My problem is..
Sun Nov 11 02:48:41 2018 TCP/UDP: Closing socket
Sun Nov 11 02:48:41 2018 SIGUSR1[soft,connection-reset] received, process restarting
Sun Nov 11 02:48:41 2018 MANAGEMENT: >STATE:1541897321,RECONNECTING,connection-reset,,,,,
Sun Nov 11 02:48:41 2018 Restart pause, 160 second(s)
Sun Nov 11 02:51:21 2018 Re-using SSL/TLS context
Sun Nov 11 02:51:21 2018 Control Channel MTU parms [ L:1623 D:1210 EF:40 EB:0 ET:0 EL:3 ]
Sun Nov 11 02:51:21 2018 MANAGEMENT: >STATE:1541897481,RESOLVE,,,,,,
Sun Nov 11 02:51:21 2018 Data Channel MTU parms [ L:1623 D:1450 EF:123 EB:406 ET:0 EL:3 ]
Sun Nov 11 02:51:21 2018 Local Options String (VER=V4): ‘V4,dev-type tun,link-mtu 1559,tun-mtu 1500,proto TCPv4_CLIENT,cipher AES-256-CBC,auth SHA1,keysize 256,key-method 2,tls-client’
Sun Nov 11 02:51:21 2018 Expected Remote Options String (VER=V4): ‘V4,dev-type tun,link-mtu 1559,tun-mtu 1500,proto TCPv4_SERVER,cipher AES-256-CBC,auth SHA1,keysize 256,key-method 2,tls-server’
Sun Nov 11 02:51:21 2018 TCP/UDP: Preserving recently used remote address: [AF_INET]79.107.166.206:1194
Sun Nov 11 02:51:21 2018 Socket Buffers: R=[65536->65536] S=[65536->65536]
Sun Nov 11 02:51:21 2018 Attempting to establish TCP connection with [AF_INET]79.107.166.206:1194 [nonblock]
Sun Nov 11 02:51:21 2018 MANAGEMENT: >STATE:1541897481,TCP_CONNECT,,,,,,
Sun Nov 11 02:51:22 2018 TCP connection established with [AF_INET]79.107.166.206:1194
Sun Nov 11 02:51:22 2018 TCP_CLIENT link local: (not bound)
Sun Nov 11 02:51:22 2018 TCP_CLIENT link remote: [AF_INET]79.107.166.206:1194
Sun Nov 11 02:51:22 2018 MANAGEMENT: >STATE:1541897482,WAIT,,,,,,
Sun Nov 11 02:51:22 2018 MANAGEMENT: >STATE:1541897482,AUTH,,,,,,
Sun Nov 11 02:51:22 2018 TLS: Initial packet from [AF_INET]79.107.166.206:1194, sid=20b98812 42a9fbd1
Sun Nov 11 02:51:23 2018 VERIFY OK: depth=1, CN=bexis.info
Sun Nov 11 02:51:23 2018 VERIFY KU OK
Sun Nov 11 02:51:23 2018 Validating certificate extended key usage
Sun Nov 11 02:51:23 2018 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Sun Nov 11 02:51:23 2018 VERIFY EKU OK
Sun Nov 11 02:51:23 2018 VERIFY OK: depth=0, CN=bexis.info
Sun Nov 11 02:51:24 2018 Connection reset, restarting [0]
Sun Nov 11 02:51:24 2018 TCP/UDP: Closing socket
Sun Nov 11 02:51:24 2018 SIGUSR1[soft,connection-reset] received, process restarting
Sun Nov 11 02:51:24 2018 MANAGEMENT: >STATE:1541897484,RECONNECTING,connection-reset,,,,,
Sun Nov 11 02:51:24 2018 Restart pause, 300 second(s)
Once I have everything setup, how I can add a new user with new password?
Just add additional secret.
/ppp secret add name=<user> profile=vpn-profile password=<password>
So i don’t need to create a new certificates? Basically I thought that I have to create new client and server certs and sign them by the same CA cert that I used for the first user or create even a new CA.
Is it safe from security perspective to share the same OpenVPN config file with embedded certificates for multiple users? What in case if one user will share my OpenVPN config file to someone else or make it public?
Only one server/client certificate is really required. Multiple users on the same certificate is ok as each user is still protected by password and encryption keys are anyhow created dynamically and not from client certificate. You are essentially at least equally protected as those using just user/pass.
Said that, having multiple client certificates will not hurt and it does allow you to control access by disabling assigned client certificate, even if user/pass combo is correct. Just create another client certificate from the same CA and you’re good. Keeping track of which certificate you give to which user is something you’ll need to do manually as Mikrotik doesn’t link them. All OpenVPN cares about it that you have valid user/pass and client certificate made by same CA as the server one.
I have current certifications as below:
CA-Certificate – CN: mydomain.com
Server-Cert – CN: *.mydomain.com
Client-Cert – CN: user.mydomain.com
In case of creating a new certs pair Server/Client how should these certificates look like? Something like below?
Server-Cert – CN: *.mydomain.com
Client-Cert – CN: user1.mydomain.com
Regards
Ok I just created cert for next user with CN=new_user.mydomain.com then signed it with my CA and it works like a charm! Now I just need to figure out, how to restrict VPN users to specific subnets…
Thanks!
Ever since the new version of Router OS you have to select cipher AES-256 instead of 128 because it wont manually switch it anymore, I had this issue just now.
Hello,
After a couple of hour I kinda made it work, but not sure this is the log file, maybe you can take a look?
Best regards
Wed Jan 30 19:29:41 2019 OpenVPN 2.4.6 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Apr 26 2018
Wed Jan 30 19:29:41 2019 Windows version 6.2 (Windows 8 or greater) 64bit
Wed Jan 30 19:29:41 2019 library versions: OpenSSL 1.1.0h 27 Mar 2018, LZO 2.10
Enter Management Password:
Wed Jan 30 19:29:41 2019 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Wed Jan 30 19:29:41 2019 Need hold release from management interface, waiting…
Wed Jan 30 19:29:42 2019 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Wed Jan 30 19:29:42 2019 MANAGEMENT: CMD ‘state on’
Wed Jan 30 19:29:42 2019 MANAGEMENT: CMD ‘log all on’
Wed Jan 30 19:29:42 2019 MANAGEMENT: CMD ‘echo all on’
Wed Jan 30 19:29:42 2019 MANAGEMENT: CMD ‘bytecount 5’
Wed Jan 30 19:29:42 2019 MANAGEMENT: CMD ‘hold off’
Wed Jan 30 19:29:42 2019 MANAGEMENT: CMD ‘hold release’
Wed Jan 30 19:29:42 2019 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Wed Jan 30 19:29:48 2019 MANAGEMENT: CMD ‘password […]’
Wed Jan 30 19:29:48 2019 WARNING: this configuration may cache passwords in memory — use the auth-nocache option to prevent this
Wed Jan 30 19:29:48 2019 MANAGEMENT: >STATE:1548869388,RESOLVE,,,,,,
Wed Jan 30 19:29:48 2019 TCP/UDP: Preserving recently used remote address: [AF_INET]86.124.85.9:1194
Wed Jan 30 19:29:48 2019 Socket Buffers: R=[65536->65536] S=[65536->65536]
Wed Jan 30 19:29:48 2019 Attempting to establish TCP connection with [AF_INET]86.124.85.9:1194 [nonblock]
Wed Jan 30 19:29:48 2019 MANAGEMENT: >STATE:1548869388,TCP_CONNECT,,,,,,
Wed Jan 30 19:29:49 2019 TCP connection established with [AF_INET]86.124.85.9:1194
Wed Jan 30 19:29:49 2019 TCP_CLIENT link local: (not bound)
Wed Jan 30 19:29:49 2019 TCP_CLIENT link remote: [AF_INET]86.124.85.9:1194
Wed Jan 30 19:29:49 2019 MANAGEMENT: >STATE:1548869389,WAIT,,,,,,
Wed Jan 30 19:29:49 2019 MANAGEMENT: >STATE:1548869389,AUTH,,,,,,
Wed Jan 30 19:29:49 2019 TLS: Initial packet from [AF_INET]86.124.85.9:1194, sid=5fcb975b ee355860
Wed Jan 30 19:29:49 2019 VERIFY OK: depth=1, CN=globalrecords.com
Wed Jan 30 19:29:49 2019 VERIFY OK: depth=0, CN=*.globalrecords.com
Wed Jan 30 19:30:49 2019 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Wed Jan 30 19:30:49 2019 TLS Error: TLS handshake failed
Wed Jan 30 19:30:49 2019 Fatal TLS error (check_tls_errors_co), restarting
Wed Jan 30 19:30:49 2019 SIGUSR1[soft,tls-error] received, process restarting
Wed Jan 30 19:30:49 2019 MANAGEMENT: >STATE:1548869449,RECONNECTING,tls-error,,,,,
Wed Jan 30 19:30:49 2019 Restart pause, 5 second(s)
Wed Jan 30 19:30:54 2019 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Wed Jan 30 19:30:54 2019 MANAGEMENT: >STATE:1548869454,RESOLVE,,,,,,
Wed Jan 30 19:30:54 2019 TCP/UDP: Preserving recently used remote address: [AF_INET]86.124.85.9:1194
Wed Jan 30 19:30:54 2019 Socket Buffers: R=[65536->65536] S=[65536->65536]
Wed Jan 30 19:30:54 2019 Attempting to establish TCP connection with [AF_INET]86.124.85.9:1194 [nonblock]
Wed Jan 30 19:30:54 2019 MANAGEMENT: >STATE:1548869454,TCP_CONNECT,,,,,,
Wed Jan 30 19:30:55 2019 TCP connection established with [AF_INET]86.124.85.9:1194
Wed Jan 30 19:30:55 2019 TCP_CLIENT link local: (not bound)
Wed Jan 30 19:30:55 2019 TCP_CLIENT link remote: [AF_INET]86.124.85.9:1194
Wed Jan 30 19:30:55 2019 MANAGEMENT: >STATE:1548869455,WAIT,,,,,,
Wed Jan 30 19:30:55 2019 MANAGEMENT: >STATE:1548869455,AUTH,,,,,,
Wed Jan 30 19:30:55 2019 TLS: Initial packet from [AF_INET]86.124.85.9:1194, sid=3b2f64a8 848eb014
Wed Jan 30 19:30:55 2019 VERIFY OK: depth=1, CN=globalrecords.com
Wed Jan 30 19:30:55 2019 VERIFY OK: depth=0, CN=*.globalrecords.com
Wed Jan 30 19:31:55 2019 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Wed Jan 30 19:31:55 2019 TLS Error: TLS handshake failed
Wed Jan 30 19:31:55 2019 Fatal TLS error (check_tls_errors_co), restarting
Wed Jan 30 19:31:55 2019 SIGUSR1[soft,tls-error] received, process restarting
Wed Jan 30 19:31:55 2019 MANAGEMENT: >STATE:1548869515,RECONNECTING,tls-error,,,,,
Wed Jan 30 19:31:55 2019 Restart pause, 5 second(s)
Wed Jan 30 19:32:00 2019 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Wed Jan 30 19:32:00 2019 MANAGEMENT: >STATE:1548869520,RESOLVE,,,,,,
Wed Jan 30 19:32:00 2019 TCP/UDP: Preserving recently used remote address: [AF_INET]86.124.85.9:1194
Wed Jan 30 19:32:00 2019 Socket Buffers: R=[65536->65536] S=[65536->65536]
Wed Jan 30 19:32:00 2019 Attempting to establish TCP connection with [AF_INET]86.124.85.9:1194 [nonblock]
Wed Jan 30 19:32:00 2019 MANAGEMENT: >STATE:1548869520,TCP_CONNECT,,,,,,
Wed Jan 30 19:32:01 2019 TCP connection established with [AF_INET]86.124.85.9:1194
Wed Jan 30 19:32:01 2019 TCP_CLIENT link local: (not bound)
Wed Jan 30 19:32:01 2019 TCP_CLIENT link remote: [AF_INET]86.124.85.9:1194
Wed Jan 30 19:32:01 2019 MANAGEMENT: >STATE:1548869521,WAIT,,,,,,
Wed Jan 30 19:32:01 2019 MANAGEMENT: >STATE:1548869521,AUTH,,,,,,
Wed Jan 30 19:32:01 2019 TLS: Initial packet from [AF_INET]86.124.85.9:1194, sid=6b8fc80e 7f0b6fec
Wed Jan 30 19:32:01 2019 VERIFY OK: depth=1, CN=globalrecords.com
Wed Jan 30 19:32:01 2019 VERIFY OK: depth=0, CN=*.globalrecords.com
To easy config openvpn in Mikrotik
https://www.youtube.com/watch?v=1VxU5UDrj7o
Or here:
https://administrator.de/content/detail.php?id=359367&token=695#comment-1349554
Unfortunately in German but the screenshot pictures and config files speak for themselves.
Hello all,
regarding the “auth-user-pass” you can create a file like auth.cfg where you adding username and password.
Create a new text file in the Configurations file; name the newly-created file “auth.cfg”, and enter the following information. Save the file one you have entered the following 2 lines:
1st line of text file: Enter only your account username
2nd line of text file: Enter only your account password
Save the file into the same location where client.ovpn and add into config file :
auth-user-pass auth.cfg
In this way, each time when you connect to the OpenVPN server will not ask your credentials.
Best Regards,
Daniel
You guys can use this site to generate the .ovpn config faster: https://ovpnconfig.com.br
Hi,
Thanks for documenting this.
Unfortunately I have a problem: the tunnel is up and running, I can ping 192.168.88.1 (Mikrotik’s IP address for internal LAN – the OpenVPN range is set to 192.168.89.0/24) but no other PCs from internal LAN. Using Wireshark I can see the ICMP request coming to PC but I don’t get a reply from it. I’ve already set proxy-arp on bridge interface. What I’m doing wrong?
please help here guys
Attempting to establish TCP connection with [AF_INET]41.144.77.73:1194 [nonblock]
Hey Man! Big thank you! Your article saved me a lot of work. I tried a couple of tutorials in the Internet but all of them sucks. You are the best. I owe you a beer!
Thanks for the tutorial. Quite helpful.
This is probably so obvious as to make these stupid questions, but…
In the following lines you specify a DHCP Pool and then a server.
/ip
pool add name=”vpn-pool” ranges=192.168.8.10-192.168.8.99
…
/ppp
profile add name=”vpn-profile” use-encryption=yes local-address=192.168.8.250
dns-server=192.168.8.250 remote-address=vpn-pool
secret add name=user profile=vpn-profile password=password
1) Does Mikrotik automatically create a dns server out of 192.168.8.250?
My Mikrotik IP address is 192.10.0.1 and the DHCP Server Range is from *.100 to *.255. My Windows Server (192.10.0.100) acts as DHCP server for users who use Folder Redirect on LAN.
2) So do I point VPN to a NEW dns-server=192.168.8.250 in your example, or to one of the existing DHCP servers?
Phillip
Okay, the second one WAS a stupid question. I missed your answer in line above quoted code. Still curious about first question.
Any of Mikrotik’s IPs can be used as DNS usually. However, I generally had a lot of issues with this as Mikrotik has lacking support for pushing DNS server-side. You can configure it on client though (check
dhcp-option DNSparameter).Hi,
Windows OVPN and Samsung Androis mobile clients are working without problem.
But iphone is after upgrade to iOS 14.7.1 OVPN not more working.
My .ovpn file with .ovpn12
client
dev tun
proto tcp
remote x.x.x.x 1194
resolv-retry infinite
nobind
persist-key
persist-tun
pkcs12 client2.ovpn12
remote-cert-tls server
tls-version-min 1.2
cipher AES-128-CBC
auth SHA1
auth-user-pass
auth-nocache
redirect-gateway def1
verb 3
—–BEGIN CERTIFICATE—–
…
—–END CERTIFICATE—–
Is this file not more valid ?
Please some working example. Thanks.
Worked just fine on a CCR1036 – thank you!
That’s true, the lack of servers are really a disadvantage, but I asked the support today and they told me that this and next month they will add around 50 servers in different countries, they are now in process with dealing with the datacenters while getting ipv4 addresses is getting more and more complex task…